Machine-Readable Security Data (Errata, OVAL, CSAF)
TuxCare provides the following security updates for ELS for OS:
Released Fixes are available via cve.tuxcare.com and can additionally be found on security.tuxcare.com.
Errata advisories
TuxCare Endless Lifecycle Support provides qualified security and selected bug-fix errata advisories across all architectures. They can help users track which CVEs are resolved and which bugs have been addressed.
You can view the full list of released fixes on cve.tuxcare.com.
OVAL patch definitions
Leveraging the Open Vulnerability and Assessment Language (OVAL) patch definitions with OVAL-compatible tools, e.g. OpenSCAP, users can accurately check their systems for the presence of vulnerabilities.
Identifying the vulnerabilities that apply to your systems is an important task for IT and InfoSec teams, and at TuxCare we make it easy. We provide OVAL data that contain instructions to the vulnerability scanner to determine the addressed vulnerabilities from the ELS updates. This section contains information about available TuxCare ELS OVAL streams.
TuxCare ELS OVAL Streams
- Alpine Linux 3.18 ELS: oval.xml
- CentOS 6 ELS: oval.xml
- CentOS 7 ELS: oval.xml
- CentOS 8.4 ELS: oval.xml
- CentOS 8.5 ELS: oval.xml
- CentOS Stream 8 ELS: oval.xml
- Debian 10 ELS: oval.xml
- Oracle Linux 6 ELS: oval.xml
- Oracle Linux 7 ELS: oval.xml
- Red Hat Enterprise Linux 7 ELS: oval.xml
- Ubuntu 16.04 ELS: oval.xml
- Ubuntu 18.04 ELS: oval.xml
- Ubuntu 20.04 ELS: oval.xml
How to use OpenSCAP with TuxCare ELS
OpenSCAP is an open source vulnerability scanner and compliance tool and it can be used to scan a system protected by TuxCare ELS. The following steps show how to produce a vulnerability report for the system:
Install the ELS release package and OpenSCAP:
yum install els-define openscap openscap-utils scap-security-guide -yBefore running a scan, make sure the system is up to date and running the latest kernel:
yum update -yReboot the system.
RPM-based system only: after reboot, remove older kernel versions:
package-cleanup --oldkernels --count=1 -yDownload the OVAL stream. For example, Ubuntu 18.04:
wget https://security.tuxcare.com/oval/els_os/ubuntu18.04els/oval.xmlRun the scan:
oscap oval eval --results results.xml --report report.html oval.xmlExamine the scan results report.
Following the example above, the scan results report will be saved to the report.html file in the current directory. This file can then be downloaded for analysis or published directly with a local web server, for example:
python3 -m http.server 8000or for python2
python -m SimpleHTTPServer 8000Assuming the above command is run from the directory with the report.html file, the webpage with the report can then be accessed on
http://<server-ip-address>:8000/report.htmlthrough a web browser.Note: the OpenSCAP report below is provided as an example. The results will vary depending on the OS and version you are scanning.
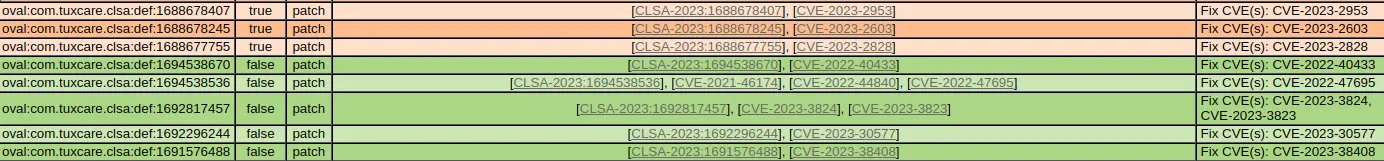
The report includes a table with vulnerabilities and their status on the examined system. A line such as the one below reports that the system is vulnerable to CVE-2023-2828:
update oval:com.tuxcare.clsa:def:1688677755 true patch [CLSA-2023:1688677755], [CVE-2023-2828] Fix CVE(s): CVE-2023-2828The table also includes corresponding hyperlinks to advisory pages where the package and the version containing the fix can be found as well as the command to run on the target system in order to install the update.
Lines like the one below designate that the fix for the corresponding CVE is already installed on the system, and no further action is needed:
oval:com.tuxcare.clsa:def:1694538670 false patch [CLSA-2023:1694538670], [CVE-2022-40433] Fix CVE(s): CVE-2022-40433
How to integrate the OVAL data with a new vulnerability scanner
Identifying the vulnerabilities that apply to your systems is an important task for IT and InfoSec teams, and at TuxCare we make it easy.
To detect whether a system has TuxCare ELS installed, check for the following file being present: /etc/els-release.
Once that is validated, you can use the OVAL files corresponding to your operating system from above to scan for vulnerabilities.
Common Security Advisory Framework
Common Security Advisory Framework (CSAF) is a machine-readable format, standardized by OASIS. It's designed to enable consistent and automated sharing of security advisory information.
TuxCare publishes the following CSAF files at security.tuxcare.com:
- CSAF Vulnerability Exploitability eXchange (VEX) files – VEX documents, indexed by CVE, are available in CSAF 2.0 format, including past CVEs.
- CSAF Security Advisory files – advisories are published in CSAF 2.0 format and indexed by Security Advisory.
provider-metadata.json contains information for tools and users about where and how to retrieve CSAF advisories published by TuxCare. By OASIS requirements, it is available at two URLs (both serving the same file):
TuxCare CSAF data
Currently, we provide CSAF data for the following OS versions:
- Alpine Linux 3.18 ELS: security.tuxcare.com/csaf/v2/els_os/alpinelinux3.18els/
- CentOS 6 ELS: security.tuxcare.com/csaf/v2/els_os/centos6els/
- CentOS 7 ELS: security.tuxcare.com/csaf/v2/els_os/centos7els/
- CentOS 8.4 ELS: security.tuxcare.com/csaf/v2/els_os/centos8.4els/
- CentOS 8.5 ELS: security.tuxcare.com/csaf/v2/els_os/centos8.5els/
- CentOS Stream 8 ELS: security.tuxcare.com/csaf/v2/els_os/centos-stream8els/
- Debian 10 ELS: security.tuxcare.com/csaf/v2/els_os/debian10els/
- Oracle Linux 6 ELS: security.tuxcare.com/csaf/v2/els_os/oraclelinux6els/
- Oracle Linux 7 ELS: security.tuxcare.com/csaf/v2/els_os/oraclelinux7els/
- Red Hat Enterprise Linux 7 ELS: security.tuxcare.com/csaf/v2/els_os/rhel7els/
- Ubuntu 16.04 ELS: security.tuxcare.com/csaf/v2/els_os/ubuntu16.04els/
- Ubuntu 18.04 ELS: security.tuxcare.com/csaf/v2/els_os/ubuntu18.04els/
- Ubuntu 20.04 ELS: security.tuxcare.com/csaf/v2/els_os/ubuntu20.04els/
TuxCare ELS RSS releases feeds
- Alpine Linux 3.18 ELS: cve.tuxcare.com/rss_feed/els/releases/alpinelinux3.18els
- CentOS 6 ELS: cve.tuxcare.com/rss_feed/els/releases/centos6els
- CentOS 7 ELS: cve.tuxcare.com/rss_feed/els/releases/centos7els
- CentOS 8.4 ELS: cve.tuxcare.com/rss_feed/els/releases/centos8.4els
- CentOS 8.5 ELS: cve.tuxcare.com/rss_feed/els/releases/centos8.5els
- CentOS Stream 8 ELS: cve.tuxcare.com/rss_feed/els/releases/centos8streamels
- Debian 10 ELS: cve.tuxcare.com/rss_feed/els/releases/debian10els
- Oracle Linux 6 ELS: cve.tuxcare.com/rss_feed/els/releases/oraclelinux6els
- Oracle Linux 7 ELS: cve.tuxcare.com/rss_feed/els/releases/oraclelinux7els
- Red Hat Enterprise Linux 7 ELS: cve.tuxcare.com/rss_feed/els/releases/rhel7els
- Ubuntu 16.04 ELS: cve.tuxcare.com/rss_feed/els/releases/ubuntu16.04els
- Ubuntu 18.04 ELS: cve.tuxcare.com/rss_feed/els/releases/ubuntu18.04els
- Ubuntu 20.04 ELS: cve.tuxcare.com/rss_feed/els/releases/ubuntu20.04els